Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Smart Meter Tampering Detection Using IoT Based Unsupervised Machine Learning
Authors: Ilokanuno C. Ogochukwu, Christiana C. Okezie
DOI Link: https://doi.org/10.22214/ijraset.2024.61153
Certificate: View Certificate
Abstract
This work presents a novel smart grid tampering detection system re-engineered for end user monitoring and pipeline automation. The research focused on distributed energy resources. In context, the end user load profile, and generation capacity were processed in the cloud environment for tampering management. Computational pipelined methodology was adopted using baseline data from an independent electricity consumption data from 2018-2021 Abuja. First, a smart grid (SG) survey was carried using existing home estate at Abuja to ascertain tampering procedures in distributed energy resource domain. From the energy survey, the system architecture was developed and implemented based on computational model curve for dynamic attack vector mitigation. An Unsupervised layered SG Architecture with local concentrator was introduced including Advanced Metering Infrastructure Smart Grid (AMI SG) gateway and control Load Balancer Docker Agent with Binomial sink.SG AMI Network packet processing Scheme and docker Orchestration were characterized for SG AMI Traffic Model. Furthermore, Smart Grid Internet of Things Coordinating Infrastructure (SG-IoT-CI) Dynamic Resource Allocation and Load Balancing/Scheduling was presented. The results showed that there was a significant improvement when leveraging SG-IoT-CI unsupervised grid management. Also, a robust distributed SG-IoT based management architecture that links the processes for end-users was developed. To determine the efficiency of the computational algorithm for SG grid deployment, an experiment was carried out on SG-IoT-CI-AMI optimization model using schemes such as K-Nearest Neighbourhood with Isolated Forest (KNN +IF), Load Prediction with Regression (LPBSVR), Support vector machine (SVM), Load Prediction with Neural Network (LPBNN), Local Outlier Factor (LOF) and Lightweight On-line Detector of Anomaly (LODA) for validation study. For Full Scale Query Response Time (FSQRT) under Open Flow security control, it was observed that the SG-IoT-CI AMI Overflow and Non-Open Flow gave 47.82% and 52.17% respectively from the simulation statistic engine. Full Scale Resource Utilization under Open Flow security aggregation layer and Non-Open Flow security aggregation layer gave 2.73% and 92.27% percentile utilization respectively. Using the unsupervised contexts, the Secure SG-IoTCI_AMI Latency for LPBSVR, Proposed KNN +IF, SVM, LPBNN, LOF and LODA gave 20.96%, 11.98%, 19.31%, 19.76%, 19.01% and 8.98% respectively. Secure SGIoTCI_AMI service rate gave 14.03%, 35.09%, 5.26%, 8.77%, 15.79% and 21.05% respectively. Secure SG-IoTCI_AMI Throughput gave 19.13%, 25.04%, 19.27%, 15.47%, 18.28% and 28.12% respectively. Secure SGIoTCI_AMI Accuracy Response gave 26.66%, 31.11%, 15.55%, 0.00%, 22.22% and 4.46% respectively. The results show that tampering control within SG grid ecosystems is feasible and very efficient.
Introduction
I. INTRODUCTION
The dream of every Nigerian is to have an automated power system with adequate supply. The current electric power systems in Nigeria that has been serving us for more than five decades lack robust automation and security. The system depends heavily on fossil fuels, including oil, coal, and natural gas, as energy sources without any form of smart initiative. These fossil fuels are non-renewable and the reserves on the earth are being consumed rapidly [1]. The present energy crisis has brought serious global attention to finding alternative energy resources that can sustain long-term industrial development. The identified renewable energy resources include wind, hydro, solar, tidal, geothermal, and waste [2]. These are referred to as green energy as they do not release carbon dioxide (CO2) into the atmosphere in the process of electric energy generation. The global consensus is that distributed energy sources should be designed to complement and possibly replace fossil fuels due to their exploitation durability and environmental friendliness. The system must be resilient and highly secured.
Active research studies and deployment activities across the world are now focusing on how to effectively harness renewable energy resources as well as the legacy grid model [2], [3], [4]. A next-generation power grid now incorporates diversified distributed energy sources, automated and intelligent management as a critical component that determines the effectiveness and efficiency of these power systems. This is called a smart grid (SG) [5]. It is an advanced electrical grid that uses composite information and communications technologies to gather and act on real-time information, such as the behavior of suppliers and consumers in an automated fashion to improve the efficiency, reliability, economics, and sustainability of the production and distribution of electricity [4], [5].
The idea behind transforming an existing electrical grid to SG is to offer stable, accessible, reliable, economic and high quality electricity while reducing environmental impacts and driving economic growths. This initiative seeks to drive energy sustainability and better service delivery to end users. Again, modernizing the existing utility grid to intelligently and efficiently respond to available power generation, power transmission and consumer demand offers numerous advantages. This comes through management automation and intelligence subsystem integration. The merits over the current systems include: flexibility, intelligence, resilience, sustainability, and customization [6]. Obviously, the SG control centers are expected to monitor and interact with the electric devices remotely in real time while other subsystems focus on enhancing the power quality as well as coordinate their local devices self-consciously [6]. Enab1ed by the significant advancements in system automation and intelligence [1], the concept of Energy Internet [7] has been proposed that envisions an exciting prospect of the future energy utilization paradigm throughout all the energy generation, storage, and transmission and distribution phases. Smart grid convoluted network (SGCN) [8] has been proposed to halt possible cyber-attacks which affects the computational requirements of SG applications, un-fortunately the security of SG supporting core infrastructures are still been compromised like the remote monitoring and control system, known as the Supervisory Control and Data Acquisition (SCADA) system, Energy Management System (EMS), power system communication infrastructure, and the computational and storage resources . Without adequate security to protect SG phasor measurement units (PMU), Wide Area Measurement systems, Substation Automation, and Advanced Metering Infrastructure (AMI), the exploitation of its vulnerabilities can lead to SG crisis. This is because the EMS usually resides in a utility control centre and performs state estimation functions, contingency analysis and automatic generation control (AGC). The EMS state estimator receives data from SCADA which is conveyed through the Inter-Control Centre Communication Protocol (ICCP) from other utility’s control centers. This data is used to estimate the operational state of the smart grid every few minutes. This gives situational awareness information which is needed by the power grid operators for making timely and informed decisions. In fact, the deployment of the above SG technologies will greatly improve the reliability of the grid and reduce costs of power delivery while presenting new dependency on cyber resources which may be open to threats and attacks. For example, a compromise of the metering networks may allow an attacker access to the control functions that, if corrupted, will threaten the availability of the data in the system and consequently violate the integrity of the system. The Advanced Metering Infrastructure (AMI) is currently regarded as the foundation of the smart grid. The AMI is responsible for the bi-directional communication of loads and user consumption data between utility companies and energy consumers. This action helps in the implementation of control signals and commands that are needed in taking necessary control actions as well as in Demand Side Management (DSM).SG AMI could be configured to integrate a couple of technologies to achieve its desired objectives. This AMI includes smart meters, communication networks, and data management systems. It also incorporates in its design a means of collecting data into software applications and interfaces.
As such, SG Internet of Things (IoT) coordination infrastructure (SG-IoT-CI) is proposed in this work. Electricity theft in the SG model will be solved via IoT unsupervised machine learning algorithm (UMLA) in SG-IoT-CI.
Current approaches mostly have relied on data acquired from utility companies for analysis that are time-consuming and very complex and which have left the problems unresolved besides its unreliability. However, this method of acquisition of such data could infringe on the privacy of consumers. Hence, the system must respect and protect the privacy of consumers even in the cloud. Instead of relying on energy consumption data alone to detect illegal consumers, this work will employ a disruptive IoT unsupervised machine learning algorithm in the smart grid AMI to detect energy theft without allowing private energy profile data of consumers to be violated. The actual metering data can be captured by analytics from the AMI micro grid switches. By incorporating cloud technology in smart grid architecture, will offer resilience for bandwidth data offloading from the edge devices (AMI) into the cloud through the fog layer.
The advantage is that the huge computational capability of the cloud datacenter for utility load stations will be relieved of the burden of storage processing, and maintenance of energy consumption data using smart type-1 virtualization technologies.
More so, preserving the privacy of consumers can be achieved by designing robust and resilient AMI communication architectures with state-of-the-art cryptographic algorithms and data aggregation protocols that will ensure the privacy and security of end user’s data in the face of different cyber-attacks. One major drawback from current approaches for providing privacy of final consumers in AMI systems for smart grid is the unavailability of predictive analytics for tampered AMI systems in a distributed smart grid system. On the other hand, the existing network platforms are highly inefficient for deploying and hosting a secured monitoring application such as the SG AMI, feedback communication, and DSM (full-duplex communication). As such, there is a need to develop a reliable SG-IoTCI that can address the limitations of traditional models while offering smarter integration with renewable micro-grid sources on metering and end-user profiling.
II. MATERIALS AND METHOD
The Open-Flow firewall is introduced in SG-IoT-AMI-infrastructure, to mitigate and dynamically handle the tampering attack vectors. In this case, DDoS (distributed denial of service) is monitored such that only legitimate traffic is allowed through the Open-Flow firewall service while using the AMI to reach the cluster-backed servers. Illegal traffic is stopped at the border, before it reaches the network. At the level of network tampering, DDoS mitigation focuses on maintaining TCP/IP web characteristics 24 hours a day, 7 days a week, independent of network conditions. To investigate and confirm the impact of the Open-Flow firewall on the SG-IoT-AMI-infrastructure, a well-designed cloud-based network was built using the parameters in Table 1.
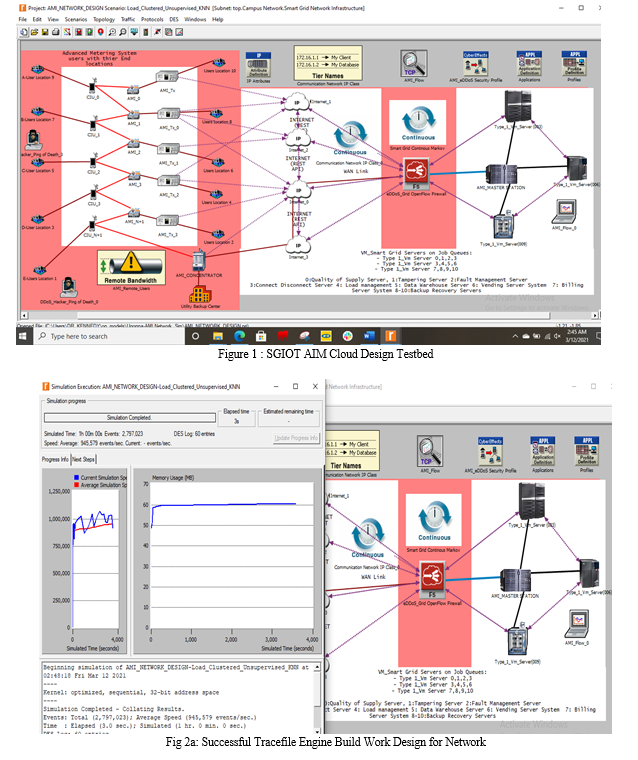
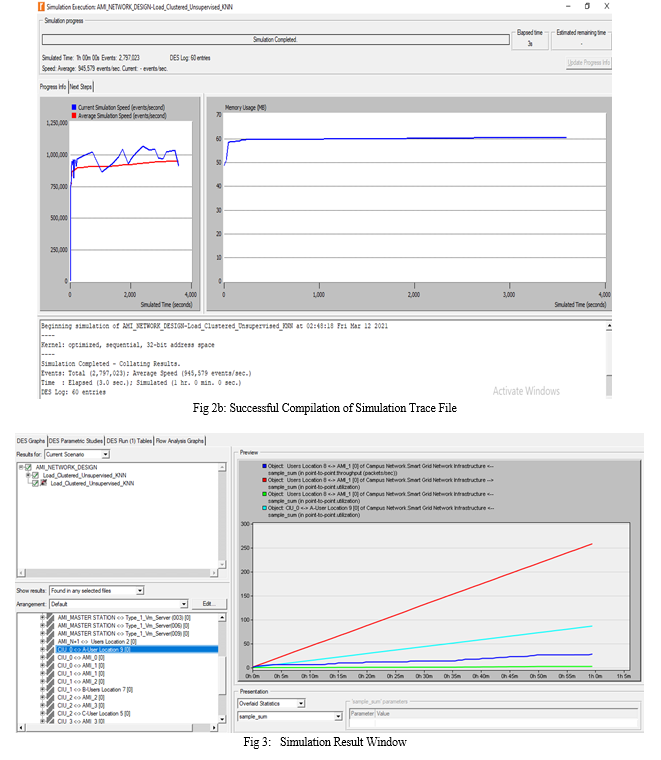
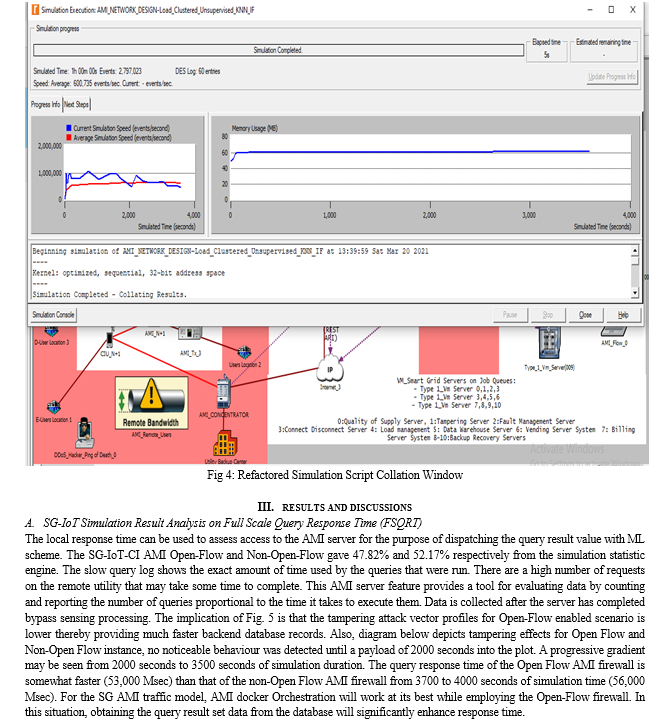
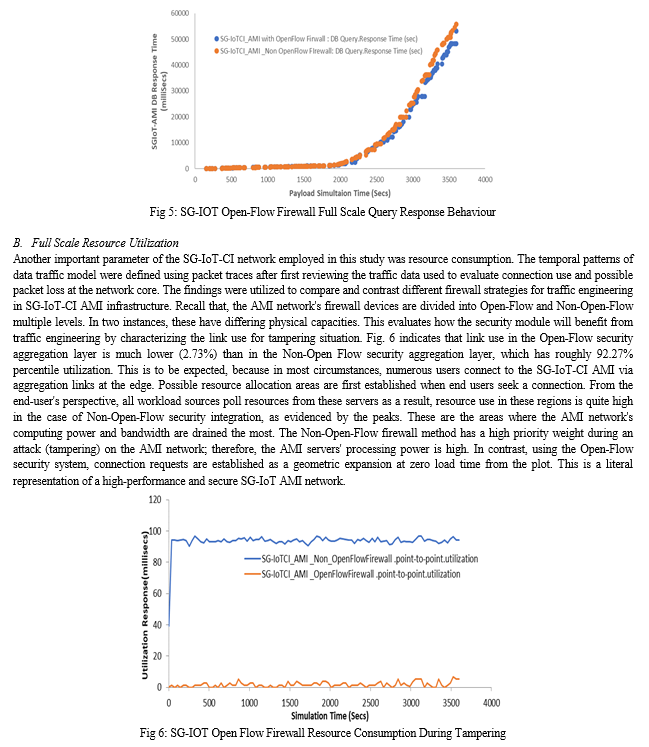
To investigate and verify the impact of the Open-Flow firewall on AMI-based infrastructure in Table 1, a hostile hacker targeted the target network with a volumetric DDoS assault flood. This was accomplished using data packets that can entirely saturate the available network bandwidth. The assault exploited a 250 Gbps bandwidth, which resulted in extremely high traffic volumes, saturating the targeted SG-IoT AMI network and server subsystems. In essence, this can result in significant service disruption for valid location-based users attempting to use the web http/TCP/IP service. In the absence of effective security mechanisms, this volumetric attack (250 Gbps DDoS), which can literally endure for longer in a production environment, can hijack and maybe bring down the entire SG-IoT AMI network within minutes. This assault is particularly noticeable at the network layer (layers 3 and 4), where it can overwhelm a server's internet connection, network resources, and network nodes that are unable to absorb the increasing traffic volumes. This work made comparison between two major DDoS attack scenarios viz: SG-IoT Open-Flow firewall and Non SG-IoT Open-Flow firewall (conventional) in a distributed cloud based smart grid system. With compatible C++ library, a simulation with Riverbed Modeller Engine 17.5 was carried out. Various layers of integration were satisfied while using the external libraries to populate and build the network map shown in Figure 1, Figures 2, and 3 depict a successful trace file engine build work design for the network and a successful simulation trace file compilation, respectively.
Table 1: SGIOT Design Parameter for Unsupervised ML Scenario
|
S/N |
Design Details |
Set up Values |
|
1 |
Number of SGIoT AMI network units |
5 – 10 (min) |
|
2 |
Number of SGIoT AMI CIU |
5 – 10 (min) |
|
3 |
Number of SGIoT AMI Concentrator |
1 (min) |
|
4 |
Number of Utility Data center backend |
1: 6 Server Clusters |
|
5 |
Number of SGIoT AMI OpenFlow Firewall |
1 |
|
6 |
Number of SGIoT AMI Maste Stations |
1:5 Server Clusters |
|
7 |
SGIOT AMI Payload |
Volumetric Traffic Model based on TCP/IP |
|
8 |
Number of SGIOT AMI Type-1 Virtual Machine Instance |
Infinity docker workload |
|
9 |
Number of SGIOT AMI Server |
Simple CPU mode |
|
10 |
Attack Vector Traffic |
DDoS 250Gbps |
|
11 |
AMI Traffic |
On-Demand DB Query |
|
12 |
Ethernet Technology |
PPTI (40Gbps) |
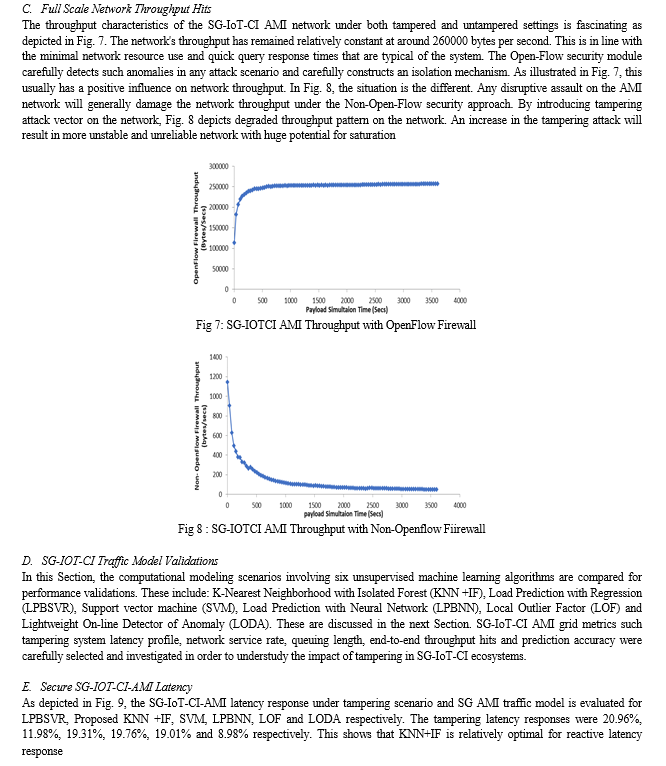
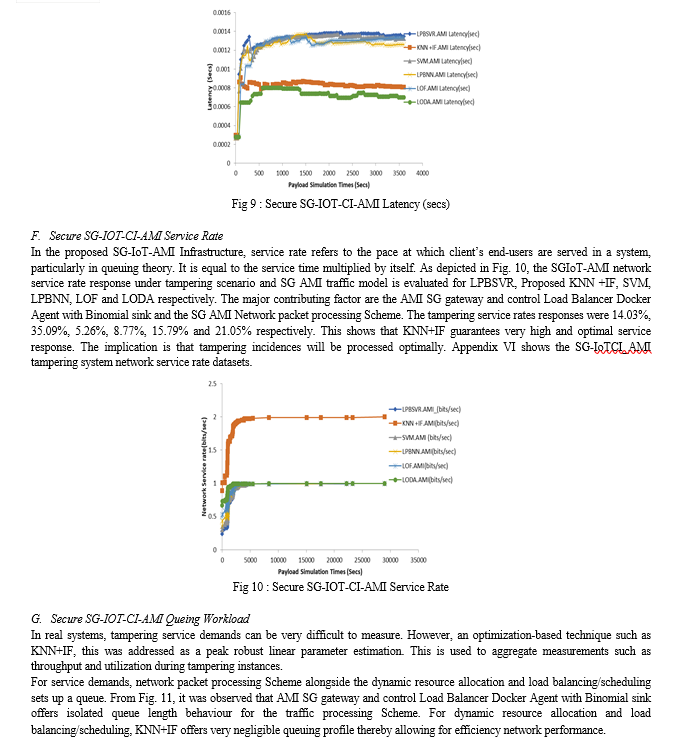
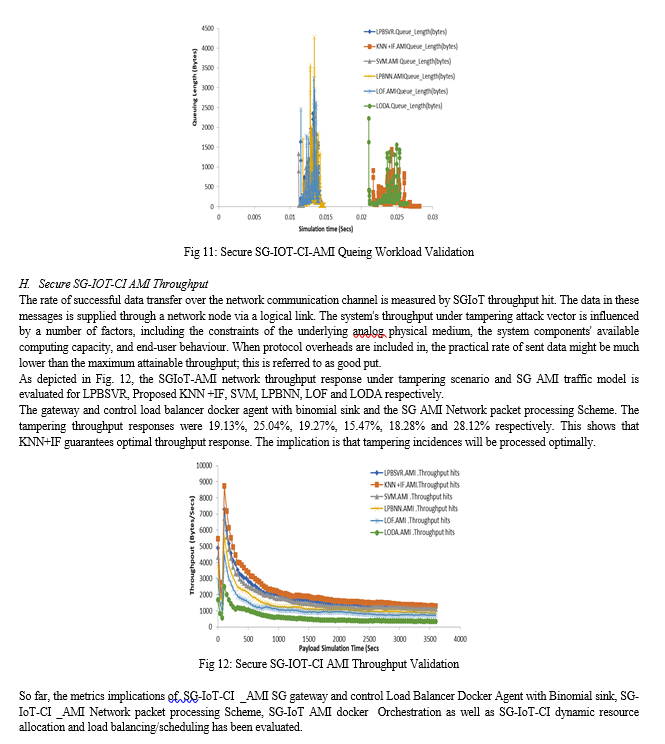
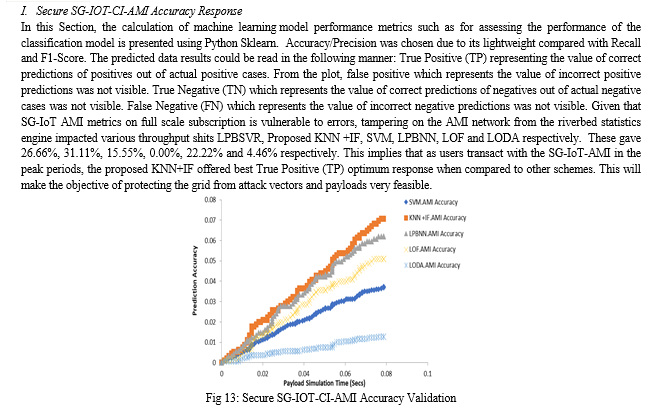
Conclusion
This paper developed a computational technique to achieve SG-IoT-CI automation for tampering mitigation suitable for Nigerian power grid. SG AMI hardware, SG hardware neural network and load management with tracking attributions were covered. First, computation models were introduced while exploring RNN with IF optimization model (RRN-IF) in the SG-IoT-CI. This was implemented to satisfy SG AMI load consumption tracking as well as Quality-of-Service (QoS) requirements. The system offers a reliable method for managing load demand using a combined symmetry of DISCO and Cloud optimization techniques. To characterize the system for efficient demand side monitoring in Nigeria, a formulation was developed for monitoring the tampered and non-untampered energy consumption via the SG probability models (Bernoulli and expanded Binomial distribution). Using SG AMI design programming, the work developed an automated SG design algorithm for energy consumption. Also, for efficient load management and consumption tracking, neural network control was achieved using C++ and embedded designs on the SG system. In context, a functional AMI hardware was built to demonstrate SG coordination while linking its processes into the Cloud for peak and off-peak demand side management for energy tampering. tampering load control of end-user services, DSM, security and QoS optimization were achieved within SG-IoTCI to satisfy the requirement of real time SG automation. SG computational process model achieved in Minitab. In this case, a computation controller for SG architecture was used for learning/training accuracy for tampered and untampered status. Also, various integration algorithms were developed and implemented from the edge to cloud. SG-IoTCI Webhook REST APIs were introduced alongside with OpenFlow (2-layer Datacenter model to solve highly complex problems of SG network supports. So far, the metrics implications of SG-IoTCI _AMI SG gateway and control Load Balancer Docker Agent with Binomial sink, SG-IoTCI _AMI Network packet processing Scheme, SGIoT AMI docker Orchestration as well as SG-IoTCI dynamic resource allocation and load balancing/scheduling has been evaluated. In the SG network validation, six schemes were used for validation on a simulated on layered architecture. In all instances of load tampering for demand side management (DSM) strategy, the unsupervised algorithm was used to enhance SG AMI transaction considering the peak load demand. Also, the algorithm provided computational matrix for prediction and isolating tampered AMIs in SG-IoTCI. Essentially, K-Nearest Neighbourhood with Isolated Forest (KNN +IF) was compared with Load Prediction with Regression (LPBSVR), Support vector machine (SVM), Load Prediction with Neural Network (LPBNN), Local Outlier Factor (LOF) and Lightweight On-line Detector of Anomaly (LODA) algorithms. S-GIoTCI Metrics such as Service delays, throughput payload, energy data received, cryptographic overhead, and Service traffic availability were carefully selected and investigated in order to understudy the impact of load scheduling on smart-grid ecosystems. The results showed that the proposed K-Nearest Neighborhood with Isolated Forest (KNN +IF) algorithm offered significant improvements.
References
[1] Infrastructurein Smart Grid”, Tsinghua Science and Technology, ISSNll1007-0214ll01/12llpp105-120,19(2), 2017. [2] J. Nagi, K. Yap, S. Tiong, S. Ahmed, and A. Mohammad, Detection of abnormalities and electricity theft using genetic support vector machines, IEEE Region 10 Conference, 2018, pp. 1-6. [3] J. Nagi, K. S. Yap, S. K. Tiong, S. K. Ahmed, and M. Mohamad, Nontechnical loss detection for metered customers in power utility using support vector machines, IEEE Transactions on Power Delivery, vol. 25, no. 2, pp.1162-1171, 2018. [4] S. Depuru, L. Wang, and V. Devabhaktuni, Support vector machine based data classification for detection of electricity theft, in Proc. 2011 IEEE/PES Power Systems Conference and Exposition (PSCE), 2011, pp. 1-8. [5] J. Nagi, K. S. Yap, S. K. Tiong, S. K. Ahmed, and F. Nagi, Improving SVM-based nontechnical loss detection in power utility using the fuzzy inference system, IEEE Transactions on Power Delivery, vol. 26, no. 2, pp. 1284-1285, 2011. [6] S. Depuru, L. Wang, and V. Devabhaktuni, Enhanced encoding technique for identifying abnormal energy usage pattern, in Proc. IEEE North American Power Symposium (NAPS),2012, pp. 1-6. [7] S. Depuru, L. Wang, V. Devabhaktuni, and R. C. Green, High performance computing for detection of electricity theft, International Journal of Electrical Power & Energy Systems, vol. 47, pp. 21-30, 2013. [8] M. A. Hearst, S. Dumais, E. Osman, J. Platt, and B. Scholkopf, Support vector machines, IEEE Intelligent Systems and their Applications, vol. 13, no. 4, pp. 18-28, 1998.
Copyright
Copyright © 2024 Ogochukwu A. Ilokanuno, Christiana C. Okezie. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET61153
Publish Date : 2024-04-28
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

